Law, Accounting, Financial Advisory
You operate in an environment where risk, confidentiality, and auditability matter. Technology failures are not inconveniences. They are liabilities.
Why this works for you
- Predictable, stable workflows
- Strong security and audit expectations
- Clear accountability at the leadership level
- Low tolerance for unmanaged systems
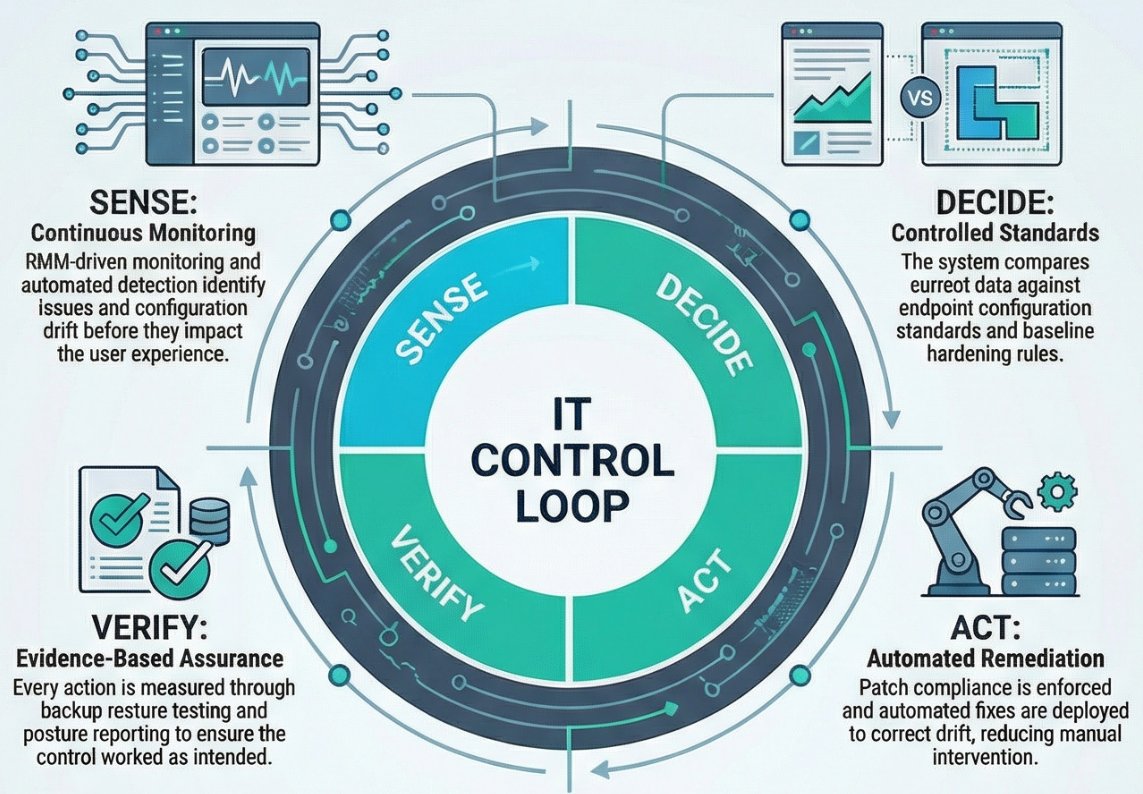
What we deliver
- Patch and configuration enforcement
- Identity and access governance
- Verified backup and recovery posture
- Executive-level risk and compliance reporting
Request a Fit Assessment